In the evolving landscape of cybersecurity, one of the most insidious and often misunderstood threats is the SS7 attack. Leveraging vulnerabilities in the Signaling System No. 7 (SS7) protocol, this attack can lead to severe privacy violations and financial losses. Here, we explore what SS7 attacks are, how they emerged, and what they are capable of doing.
What is the SS7 Protocol?
SS7, or Signaling System No. 7, is a set of telecommunication protocols developed in the 1970s. It facilitates the exchange of information needed to establish and manage telephone calls, text messages, and mobile data across different networks worldwide. SS7 is crucial for:
- Routing calls and texts.
- Enabling roaming by allowing users to access their home network services while abroad.
- Supporting billing operations.
Despite its importance, SS7 was designed in an era when trust among telecom operators was a given. Security was not a primary consideration, leaving the protocol vulnerable to exploitation.
How Did SS7 Attacks Emerge?
The vulnerabilities in SS7 began to attract attention as mobile communication grew more complex and interconnected. Initially, only large telecom operators could access SS7 networks, but with the rise of Voice over IP (VoIP) providers, smaller players gained access as well. This broader access created opportunities for malicious actors.
By the early 2010s, researchers and hackers started demonstrating how SS7 vulnerabilities could be exploited. High-profile incidents and proof-of-concept attacks brought the issue into the spotlight, showcasing the protocol’s lack of authentication and encryption as a critical flaw.
What Can an SS7 Attack Do?
SS7 attacks exploit the trust-based architecture of the protocol to execute various malicious activities. Here are some of the most concerning capabilities:
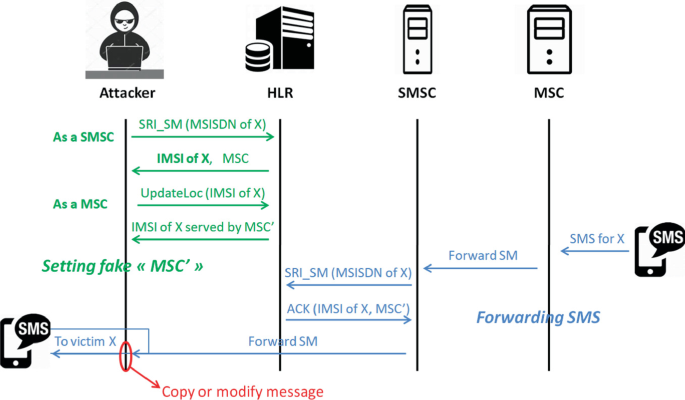
1. Call and Message Interception
Attackers can intercept phone calls and text messages, gaining access to sensitive information such as personal conversations or one-time passwords (OTPs) used for two-factor authentication.
2. Location Tracking
By querying the network, attackers can track the real-time location of a targeted mobile device. This can be used for stalking, espionage, or other nefarious purposes.
3. Fraudulent Transactions
Intercepting OTPs enables attackers to bypass two-factor authentication systems, facilitating unauthorized access to banking or online accounts.
4. Denial of Service (DoS) Attacks
Attackers can disrupt communication by flooding the network with malicious queries, rendering the target’s phone unusable.
Real-World Examples
- Banking Fraud: Criminals have used SS7 vulnerabilities to intercept OTPs sent via SMS, enabling unauthorized withdrawals from victims’ bank accounts.
- Surveillance: State-sponsored actors have reportedly exploited SS7 to spy on individuals by tracking their location and intercepting communications.
Mitigation and Prevention
While SS7 vulnerabilities are inherent to the protocol, steps can be taken to reduce the risk of attacks:
For Telecom Providers
- Implement firewalls specifically designed for SS7 traffic to detect and block malicious requests.
- Monitor SS7 traffic for unusual patterns indicative of an attack.
- Transition to newer protocols like Diameter, which offer improved security.
For Users
- Use end-to-end encrypted messaging apps for sensitive communication.
- Avoid relying solely on SMS-based two-factor authentication; consider app-based or hardware token authentication methods.
- Regularly monitor financial accounts for unauthorized activity.
The Road Ahead
The SS7 vulnerability highlights a critical lesson in cybersecurity: protocols designed without robust security measures can become significant liabilities as technology evolves. While telecom operators and governments are taking steps to address these issues, the widespread use of SS7 means the threat will persist for the foreseeable future. Awareness and proactive measures are essential to mitigate the risks associated with SS7 attacks.